Table of Contents
Last update on
Have you ever heard that 4,700,000 WordPress sites fall victim to hacking yearly?
WordPress is known to be a relatively safe content management system (CMS), but due to its popularity, it is also highly targeted by hackers. If your site becomes a target of an attack, it could harm your reputation and affect your sales performance. Safeguarding your WordPress website with the most effective security best practices is essential for maintaining trust and loyalty amongst your clients.
In this guide, you will learn:
- The 16 WordPress security best practices to safeguard your website.
- The 7 most frequent WordPress security risks that your website often faces.
- What to do if you get hacked.
How to Master WordPress Security Best Practices
The most important WordPress security best practices for your website cover vital areas such as login security, updates, and file permission controls. Go over all of them and discover the tools and plugins that can make your job easier while protecting your website.
1. Update All Your Plugins, Themes, and WordPress Core
🏆 Quick-win: By Updating your plugins, themes, and WordPress core, you avoid many security issues. Updates often include patches for vulnerabilities that hackers could exploit, so get rid of outdated themes and plugins and opt for the latest version.
✅ Best practices:
Update everything manually.
- To update WordPress core, go to Dashboard > Updates. You should then see the latest version installed:
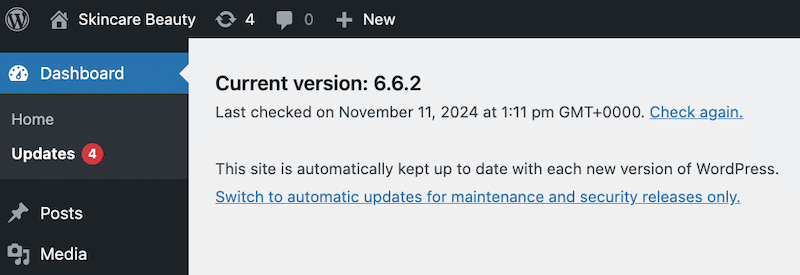
- For plugins and themes, go to Plugins > Installed Plugins or Appearance > Themes and click Update for each item.
Or consider activating auto-updates always to keep your site(s) updated.
- Go to Plugins > Installed Plugins > Select all > Enable Auto-updates.
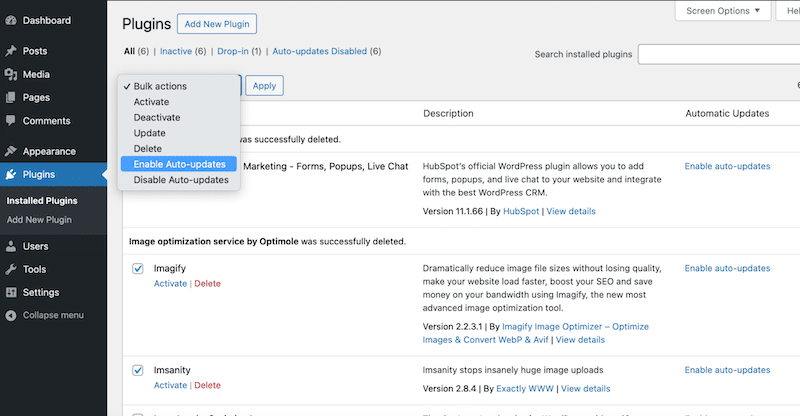
🛠️ Tools and plugins:
- WPUmbrella: It’s a reliable WordPress maintenance service that monitors your WordPress site’s safety.
- MainWP: It’s a handy self-hosted dashboard for managing multiple WordPress sites simultaneously. It is ideal to update everything automatically and save time.
- ManageWP: It’s a powerful tool that lets you view, manage, and update all your sites in one place.
2. Remove All the Nulled and Unused Plugins
🏆 Quick-win: Nulled plugins are unsafe because they lack security patches, creating vulnerable entry points on your WordPress site. Similarly, remove unused plugins to avoid hackers creating backdoors in a plugin you don’t even use.
✅ Best practices:
- Go to Plugins > Installed Plugins. You can deactivate and delete any plugins you don’t need or use anymore.
- Regularly audit plugins and remove any unnecessary ones.
🛠️ Tools and plugins:
- Health Check & Troubleshooting: It helps identify plugin conflicts and issues.
- Wordfence Security: It can help identify malicious plugins.
3. Change the Default “Admin” Username
🏆 Quick-win: Make your username harder to find for botnets to reduce the likelihood of brute force attacks.
✅ Best practices:
- Go to Users > All Users in your WordPress admin dashboard.
- Edit the “admin” user and change the username to something unique.
- Create a new user with an Administrator role, assign it a unique username, and delete the original “admin” user.
4. Define User Roles Properly
🏆 Quick-win: Assign roles carefully to limit access and increase security.
Example: A guest writer should only have access to write posts and should see different content from the WooCommerce shop owner role.
✅ Best practices:
- Go to Users > All Users to edit or assign user roles.
- Be sure that each user has only the permissions they need.
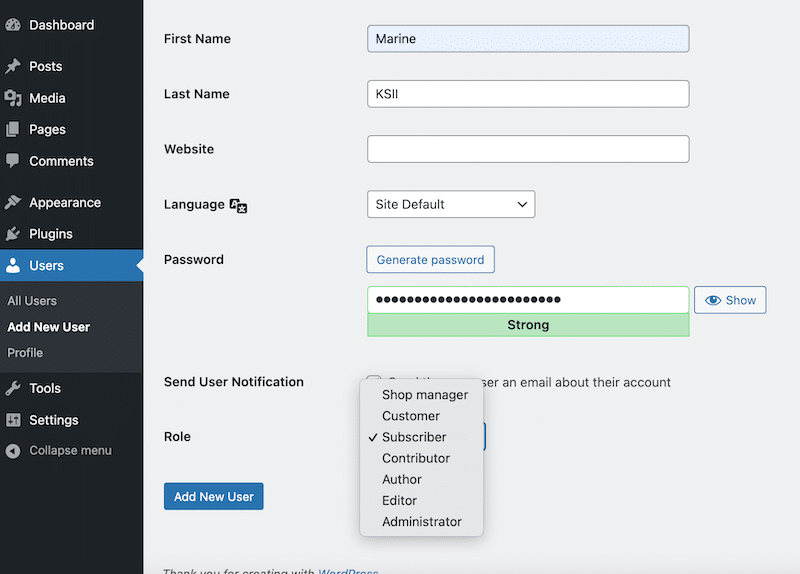
🛠️ Tools and Plugins:
- User Role Editor: Customize user roles with more than the default five roles in WordPress.
- Members: Plugin for creating and managing custom roles.
5. Use Strong Passwords with Two-Factor Authentication (2FA)
🏆 Quick-win: Use automatically generated passwords and change them regularly. Two-factor authentication (2FA) requires a second form of identification and your password to reinforce security when you log in. It could be a one-time password (OTP) sent via SMS, WhatsApp, a simple email, or even a QR code.
✅ Best practices: When creating a new password, avoid easy-to-guess ones like “admin123” or “password.” Follow those best practices instead:
- A strong password means using uppercase, lowercase, special characters, and numbers.
- Change passwords regularly across platforms (cPanel, FTP, WordPress Admin, etc.)
- Implement 2FA to add an extra layer of security when one of your users wants to connect to your site admin.
🛠️ Tools and plugins:
- WP2FA: It simplifies the process of setting up 2FA.
- Google Authenticator: A simple app to generate OTPs for secure login.
6. Implement reCAPTCHA on Forms (Including Login Page)
🏆 Quick-win: reCAPTCHA is one of the best ways to protect your site from bots and attacks on WordPress. It checks that the user is real when submitting a form. This extra layer of security prevents brute-force login attempts and unwanted spam.
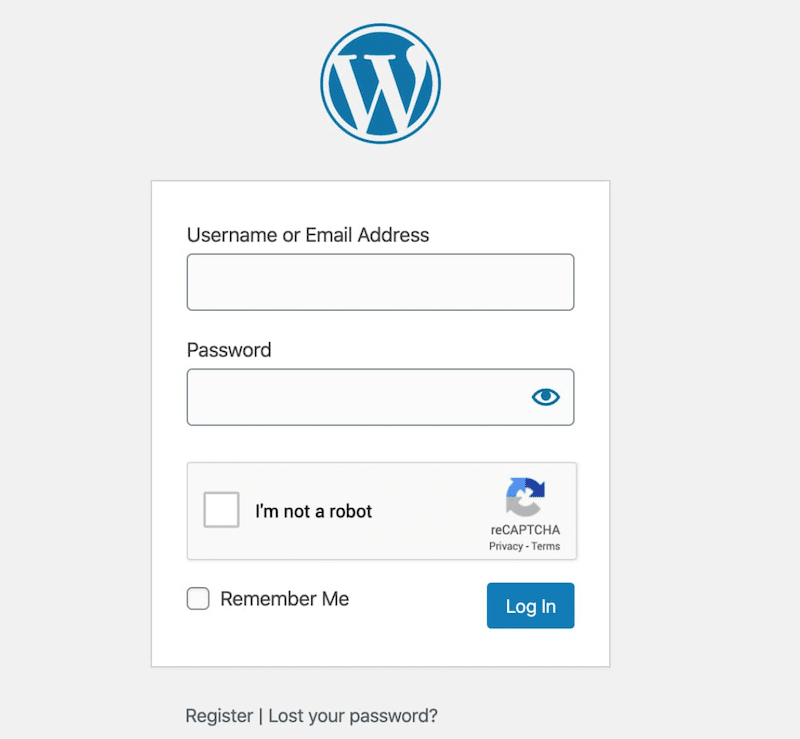
✅ Best practices:
- Add the reCAPTCHA option to your login page, registration forms, and any other user content-generated forms. This will help to stop automated submissions.
- Make sure that your reCAPTCHA version is always up-to-date.
🛠️ Tools and Plugins:
- Advanced Google reCAPTCHA: It’s one of the best plugins to add reCAPTCHA to any form, including on your WordPress login page.
7. Limit Login Attempts and Hide the wp-admin Login URL
🏆 Quick-win: Limiting login attempts reduces the risk of brute force attacks, while hiding your wp-admin login URL makes it harder for hackers to target your site.
✅ Best practices:
- Always set a limit on failed login attempts. For example, it’s recommended to allow only three unsuccessful attempts. Then, you can tell the users to return in 15 minutes for another trial).
- Change the default “yourwordpresssite.com/wp-admin” URL to something more unique and challenging to guess, such as “yoursite.com/welcome-to-your-account.”
🛠️ Tools and Plugins:
- Limit Login Attempts Reloaded: It lets you easily limit the number of login fails on your site.
- WPS Hide Login: It allows you to change the URL of the login form page to the one of your choice.
8. Use a Firewall (WAF)
🏆 Quick-win: A firewall helps in blocking connections from malicious IP addresses. It prevents a hacker from stealing your credentials and logging into your site.
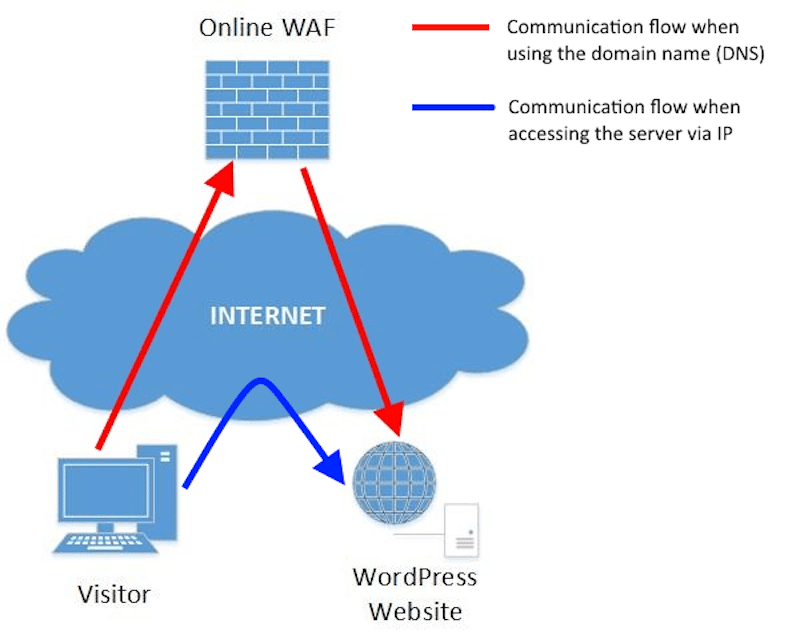
✅ Best practices:
- Enable Web Application Firewall (WAF) to block suspicious traffic before it reaches your server.
- Configure firewall settings to filter out traffic from known malicious IPs and botnets.
- Disable XML-RPC if not required, as it’s a common attack target.
🛠️ Tools and Plugins:
- Wordfence Security or Sucuri Security can identify and block malicious traffic and protect your WordPress site against threats like brute force attacks, DDoS, and malware.
9. Regularly Scan Your Site for Malware
🏆 Quick-win: Regular malware scans help detect and remove harmful code that could damage your site or compromise sensitive data.
✅ Best practices:
- Run malware scans weekly and monthly to detect and clean up any virus.
- Set up alerts to receive email notifications of any detected emergency threats.
- Make sure you choose themes, plugins, and WordPress core files that are malware-free. Also, check some of the testimonials before purchasing.
- Always keep your database clean and up-to-date.
🛠️ Tools and Plugins:
- SiteCheck (by Sucuri) and Wordfence Security to scan your site and identify potential hacks.
- WP Rocket: It’s the easiest performance plugin for WordPress that can optimize your database in one click. It’s also the most powerful tool to improve your loading time, boost your PageSpeed performance score, and optimize your Core Web Vitals.
10. Perform Regular Backups
🏆 Quick-win: By performing regular back-ups, you can quickly restore a clean version of your site if anything goes wrong.
✅ Best practices:
- Implement a strategy to run automated backups without manual efforts. This way, your weekly backups will always be done.
- We recommend you store backups in multiple locations to ensure that you can retrieve any version if, for example, your cloud fails.
- Test your backups occasionally to ensure they can be restored properly.
Tools and plugins: Use your hosting provider’s backup tool via cPanel or plugins like UpdraftPlus for seamless backup management.
11. Disable File Editing
🏆 Quick-win: Prevent unauthorized access to your theme and plugin files through the WordPress admin area, reducing security risks.
✅ Best practices: If you are comfortable with code editing, we recommend you add the following line to your wp-config.php file to disable file editing:
// Disallow file edit
define( 'DISALLOW_FILE_EDIT', true );By doing this extra security step, even if an attacker gets access to your WordPress admin, they won’t be able to modify any critical files.
🛠️ Tools and plugins: You can use the free version of the Sucuri plugin to automatically turn off file editing if you don’t feel like editing any code manually.
12. Install an SSL Certificate (HTTPS)
🏆 Quick-win: Thanks to SSL certificates, your website can easily switch from HTTP to HTTPS. HTTPS encrypts data between users and servers and helps you secure your website.
✅ Best practices:
- Get an SSL certificate from your hosting provider. Most of them include it in their plans.
- Make sure to update it because a website’s security certificate lasts for about one year.
🛠️ Tools and plugins: Most hosting providers offer SSL certificates, or you can use the Let’s Encrypt tool for free.
| 💡 Hint: By adding a small padlock icon to the browser, HTTPS serves as a trust indicator for users, giving them peace of mind that their data is secure. Additionally, it keeps potential buyers from abandoning their shopping carts due to security concerns. |
13. Disable Directory Indexing and Browsing
🏆 Quick-win: Prevent hackers from discovering vulnerabilities and sensitive files by blocking access to your directory structure.
✅ Best practices:
Disable directory browsing by adding the following line at the end of your site’s .htaccess file:
Options -Indexes - By doing this, hackers won’t see a list of files in your directories that they could use against you. Make sure the. htaccess file is visible in your hosting file manager or FTP client if you are unable to see it.
🛠️ Tools and plugins: You can use FTP or your hosting provider’s file manager to update the .htaccess file.
14. Automatically Log Out Inactive Users in WordPress
🏆 Quick-win: To reduce the risk of unauthorized access, you should automatically log out inactive (idle) users. Attackers often use inactive sessions to hack accounts and passwords (especially if users leave their devices unattended).
✅ Best practices:
- Add a setting to automatically log out idle users to ensure the session data isn’t exposed unnecessarily.
🛠️ Tools and plugins:
Idle User Logout and Inactive Logout: They automatically log out users after a set period of inactivity to prevent unauthorized access from open sessions.
15. Install a Reputable WordPress Security Plugin
🏆 Quick-win: An all-in-one security plugin helps centralize your website protection by providing essential features in one single place. This will save you time and effort!
✅ Best practices:
Look for plugins that come with the following features:
- Malware & threat protection with firewalls, malware scanning, DDoS protection, and IP blocking to prevent malicious activity.
- Access control & authentication secures user access with two-factor authentication (2FA), limits login attempts, and manages user roles.
- Site integrity & backup to ensure your site can be restored after a breach.
- Monitoring & alerts track threats and notify you of suspicious activity.
- Maintenance & updates keep your site secure through automatic updates and SSL management.
- Spam filters and other tools to secure sensitive areas of your site.
🛠️ Tools and plugins:
- Wordfence Security: It’s a highly trusted WordPress security plugin with real-time protection, malware scanning, and firewall capabilities.
- Sucuri Security: It is known for its malware detection, website monitoring, and DDoS protection features.
16. Use a Security-First Hosting Provider
🏆 Quick-win: A secure hosting provider is the foundation of your entire security strategy, as it ensures your site is protected from the server level, minimizing risks of attacks and downtime.
✅ Best practices:
- Read online reviews to evaluate the provider’s reputation for handling security issues and providing customer support. Look for features such as firewalls, DDoS protection, and daily backups.
- Choose a host with 99% uptime guarantees and fast servers for optimal site performance.
- Opt for a user-friendly dashboard for easy management of security settings.
🛠️ Plugins and tools: Consider using SiteGround or Kinsta, both known for their top-tier security protocols and reliable performance.
| 💡Hint: Read more about the best WordPress-managed hosting provider in our dedicated guide. |
Top 7 WordPress Security Issues
According to Jetpack, weak user credentials and outdated plugins are the main entry points for hackers – but there’s more. Here you can find the primary security threats facing WordPress sites today, with stats and real-world examples.
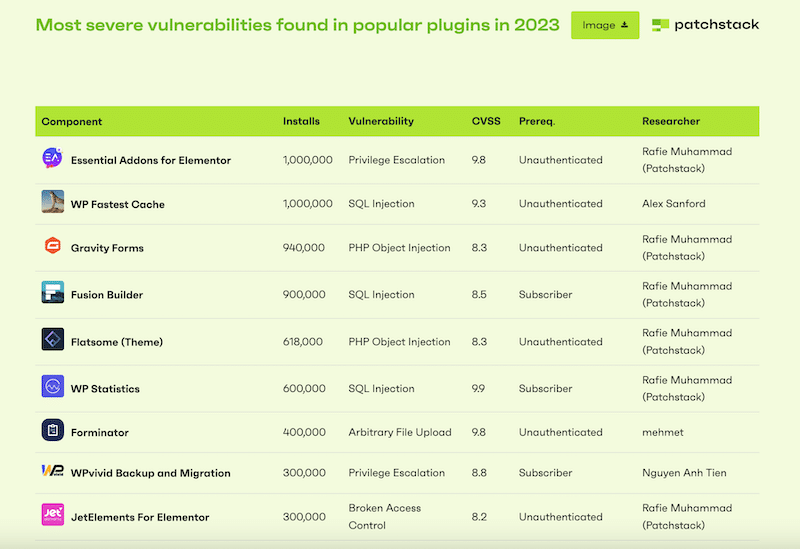
1. Vulnerabilities in Plugins
If you’re running inactive or outdated plugins on your WordPress website, remember that they might not include the latest security updates provided by the developers. Developers of themes and plugins frequently release updates to address vulnerabilities, but failing to use the versions could expose your site to attacks.
📈 Stats:
- According to a recent analysis by Patchstack, 97% of WordPress security problems are caused by plugins.
- Additionally, MelaPress found that only 30% of WordPress users have auto-updates activated on their websites.
💡 Example: In 2023, serious issues were discovered in plugins such as WP Fastest Cache and Essential Add-ons for Elementor. Developers urged users to update to the latest version as soon as possible.
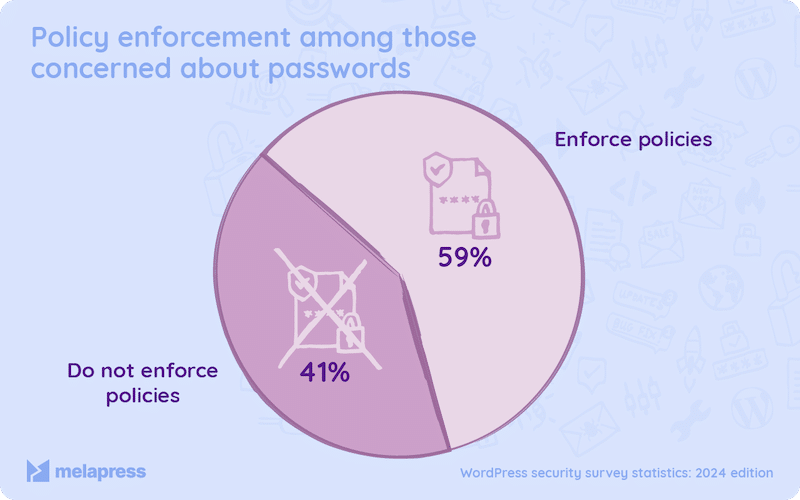
2. Brute Force Attacks (Weak Passwords)
Brute force attacks involve repeated login attempts to guess passwords until the hacker gets access to your site. They use bots that combine thousands of different combinations of usernames and passwords until they find the right one.
📈 Stats: According to a study from Melapress, 41% of their WordPress user responders are not using two-factor identification (2FA) or a strong enough password.
💡 Example: Those bots could find a password like “ADMIN123” in seconds and grant unauthorized access to your entire website.
3. Broken Access Control and Mismanaged and Undefined User Roles
Broken access control is a severe security risk that gives unauthorized people access to private information they shouldn’t have. This raises the possibility of security breaches and exposes private information to the wrong people.
📈 Stats: According to Patchstack, in 2023, 12.9% of WordPress security issues were due to broken access control.
💡 Example: Assigning editor-level access to guest writers without restrictions can lead to unwanted changes or data leaks.
4. Cross-Site Scripting (XSS) Attacks
Cross-site scripting (XSS) is a security issue that allows an attacker to inject malicious JavaScript into your code. This hurtful code is unknowingly executed by the victims and reveals their login and passwords to the attackers. Once they have the credentials, they can impersonate users.
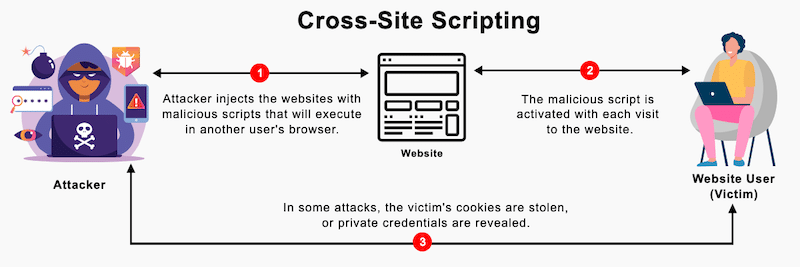
📈 Stats: According to Patchstack, In 2023, XSS attacks made up 53.3% of all new vulnerabilities in the WordPress ecosystem.
💡 Example: An attacker injects malicious scripts into your site’s comment section. As your site stores this comment in your database, the hacker can execute the harmful code when unsuspecting users view the page. This could potentially result in stealing their login information.
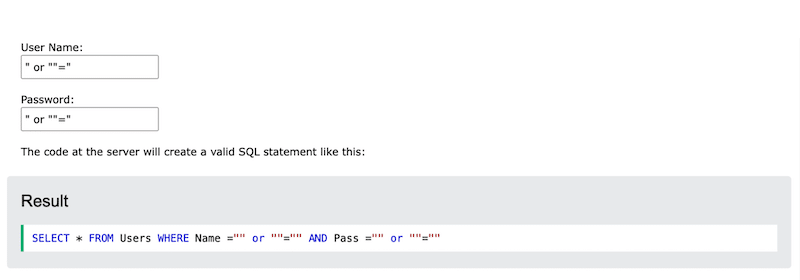
5. SQL Injection Attacks
SQL injections allow attackers to add malicious code to database queries, potentially exposing confidential information. This can allow attackers to retrieve confidential data.
📈 Stats: According to WPHackedhelp, around 20% of hackers perform SQL attacks. The most common victims are e-commerce sites built on WooCommerce.
💡 Example: A hacker might get access to usernames and passwords in a database by simply inserting ” OR “”=” into the user name or password text box:
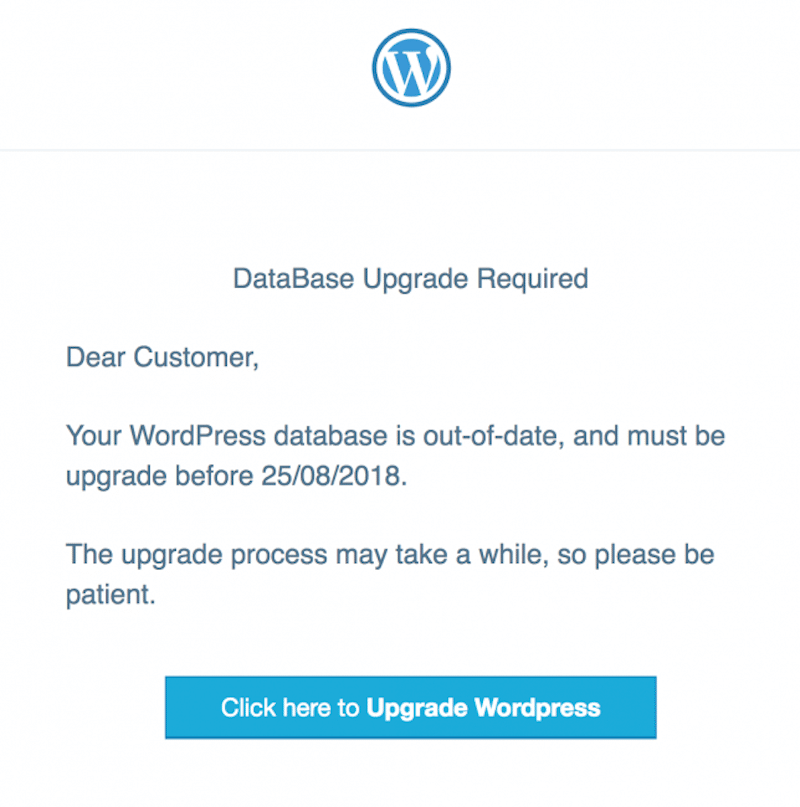
6. Cross-Site Request Forgery (CSRF) Vulnerabilities and Phishing
Phishing tricks users by imitating legitimate site pages. They provide sensitive information without knowing that a hacker is actually collecting the data.
📈 Stats: In 2023, almost 17% of security issues came from CSRF.
💡Example: A typical phishing attack would be that some hackers create a fake login page for a WordPress site. Users think it’s safe and put their credentials that are actually “captured” by those hackers.
7. Denial of Service Attacks (DoS and DDoS) and Poor Hosting
Choosing reliable and safety-first hosting is essential to protect your site from DoS and DDoS attacks. Those security issues overflood the servers and make your site temporarily inaccessible to legitimate users.
💡 Example: Your competitor launches a DDoS attack on your eCommerce WordPress site during a significant sales period. Your site becomes unavailable, and you lose some revenue. The example is a bit extreme, but you get the idea.
You are now familiar with the best security practices and the different sources of attacks on WordPress! However, your site can still get compromised even if you implement a robust security strategy. The following section outlines the necessary steps to reclaim control over your site if such a thing happens.
What to Do if Your WordPress Site Has Been Hacked
If your WordPress site is hacked, follow our guidelines below to regain control and improve its security quickly.
1. Put Your Site Offline
You should temporarily put your site offline or in maintenance mode to prevent further access. This limits the spread of malware in other WordPress files and protects your visitor’s data.
2. Change All Passwords
Update passwords for all accounts linked to your site—WordPress admin, hosting account, FTP, database, and email. Use strong, unique passwords to prevent further breaches.
3. Contact Your Hosting Provider
Reach out to your hosting provider; many offer hacked-site assistance and can scan for server-level issues. Be ready to answer these questions to speed up the process:
- Can you access your WordPress admin?
- Are there suspicious links or new content on your site?
- Is Google flagging your site for security issues?
- Is your site redirecting to another URL?
4. Scan for Malware
It’s time to install a security plugin like Wordfence or Sucuri if you can still access your WordPress admin. These plugins will find the malicious files and perform malware scans to pinpoint the attack’s source.
5. Restore a Clean Backup
If you have a recent backup, restore your site to a clean version. Be sure the backup is from a date before the attack to avoid reintroducing harmful files.
6. Contact a WordPress Security Company
If you need expert help, consider hiring a WordPress security service. For example, WPBeginner Pro offers hacked-site repair for a one-time fee of $249, providing a fast solution.
Wrapping Up
In conclusion, you now know the best practices to safeguard your WordPress site, as well as the most common sources of attacks. Security standards revolve around essential actions: securing your login page, creating strong passwords, and keeping plugins clean and consistently updated. Providing a secure site is vital for your reputation—imagine the consequences if a client received a data breach notice warning that their credit card was compromised due to a lack of security measures. You don’t want that to happen!
Beyond security, performance and loading speed also play a crucial role in building trust. Once you’ve secured your site with the right tools, consider enhancing its speed with a plugin like WP Rocket.
WP Rocket is one of the best performance plugins, and it applies 80% of performance best practices upon activation. It also offers a 14-day money-back guarantee, so you don’t take any risks.
It looks like it’s time to have a WordPress site that’s both secure and lightning-fast!



